Key Benefits
Discover the unique advantages that make IntelliSec the ultimate choice for your business.
On-prem Deployment
Hyper-configurable to monitor just what your business needs & scales - covering your whole infrastructure.
Your data never leaves
The Core system and the Intelli Persist is deployed on-prem, ensuring your data never leaves your environment & it is super-fast & scalable.
Powerful dashboard
Centralized Dashboard & full Admin Panel that allows you to manage and understand your whole security infrastructure security in plain English.
Integrate with others
Easy integration with other security tools and platforms to enhance your overall security posture.
How IntelliSec Works
Lightweight agents on your endpoints write encrypted IntelliSnapshot files, which are processed by the Core System that makes the smart security conclusions and renders everything in a very human-friendly alerts in IntelliDashboard.
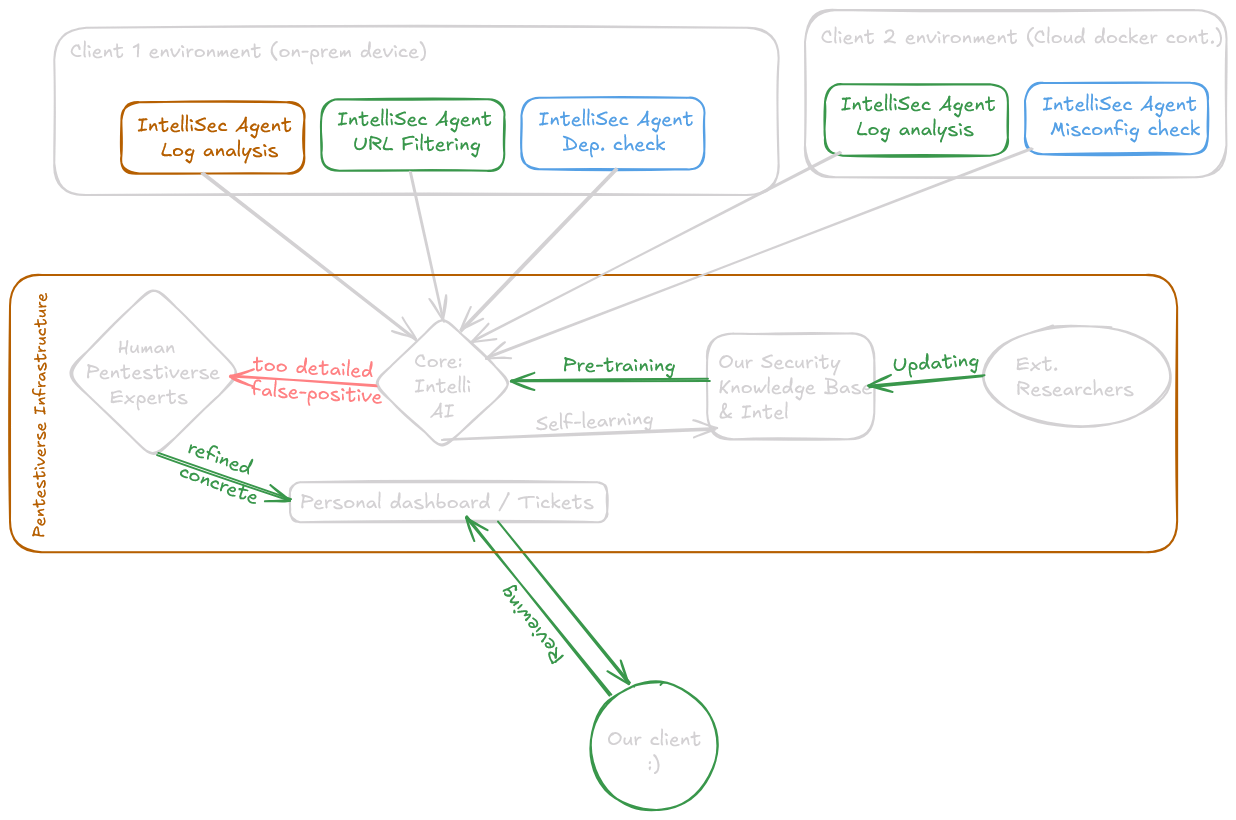
Scalable Agents
Once deployed, lightweight agents start collecting relevant security data from your endpoints safely and saving it locally encrypted in a secure snapshot file. This allows us to scale and handle one or millions of endpoints with minimal performance impact.
LLM as a consultant
We don't trust LLM's just enough to allow them to do decision making for your business, but we trust ours enough to help in augmenting and explaining vulnerabilities that our team trained it on.
Security Expert Support
When dashboard alerts are not enough, our security experts are available on-demand to help you interpret complex findings, recommend remediation steps, and provide guidance on improving your overall security posture.
Technical Specifications
What IntelliSec Monitors
Every organization faces different threats. During onboarding, you will use a checklist to define which security domains matter most for your business. The version that is deployed will then monitor those specific areas in depth:
Vulnerability Intelligence
We correlate endpoint configurations, installed software versions, and patch levels against known vulnerabilities from CVE databases to identify exploitable weaknesses and inform you near real-time. Isn't that cool?
Proactive DefenseApplication & Permission Control
Track every software installation, monitor blacklisted applications, detect suspicious permission escalations, identify unsigned drivers with complete endpoint software visibility.
Endpoint GovernanceNetwork & OS Integrity
Analysis of suspicious network activity, unauthorized open ports & services, and OS integrity checks to detect rootkits.
Data Loss PreventionCompliance & Audit Readiness
Automated compliance checking against CIS Controls and NIST Cybersecurity Framework. Augmenting our agents with compliance-specific monitoring rules to help you stay audit-ready.
CIS & NISTForensic-Grade Logging
Deep system log analysis, security event correlation, and forensic trail maintenance. Human-friendly correlation per user, time, and endpoint to facilitate investigations.
Incident ResponseCustom Security Policies
You can inform us of any custom security policies or compliance requirements during onboarding, and we will build monitoring rules tailored to your organization's needs.
Your Rules, Your WayPricing & Compliance
Flexible subscription model with enterprise discounts and compliance-ready monitoring
Subscription Pricing
per endpoint per month
Billed monthly. Cancel anytime.
- Custom-built agents with YOUR selected security rules
- Isolated infrastructure per client (Core, LLM, DB, Dashboard)
- Periodic monitoring with 5-minute collection cycles
- LLM-powered augmentation with NIST/CIS context
- Expert security team support for critical findings
Volume Discounts:
Compliance & Standards
CIS Controls
Center for Internet Security baseline compliance
NIST Framework
Cybersecurity Framework implementation
IntelliSec agents continuously verify your endpoints against CIS Controls and NIST Cybersecurity Framework requirements. We provide dyou a detailed report highlighting compliance status, gaps, and remediation recommendations to help you stay audit-ready.
Supported Certifications:
Translating complexity.
Into human-friendly actions.
Having Intellisec frees your business to depend on vendors that want to control your data.
Book Your Free Coordination Call
No sales pitch. No obligation. Just a 15-minute conversation with Pentestiverse security expert about your threat landscape, compliance gaps, and how custom endpoint intelligence can address your specific challenges.